If you want to learn how computers work and communicate with each other, you need to understand a few tools and technologies to get involved in networking. Let's explore this topic together, and you will discover many new technologies that you may recognize but do not understand how they work or their purpose.
Client-Server Architecture
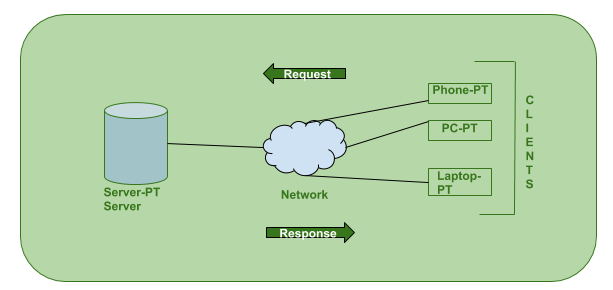
The client-server architecture is very easy to understand. In this case, the client (or our browser) sends a request to the server to get the data that the user has requested. For example, when you order food from a restaurant, you place the order with the restaurant, they prepare the dishes and send them to a delivery boy who delivers the food to you. In this example, the person who placed the order is the user, and the restaurant is the server. The client wants to make a connection with the server to get data, so the client makes a request and sends it to the server. The server will respond with the requested data.
IP Address
An IP address is a term you may have heard several times, but do you know what it means? An IP address serves as a network address, similar to how a delivery boy requires a physical address to deliver food to our homes. Computers also require an IP address to send and receive data from servers. An IP address consists of 32 bits, where each bit represents a value of either one or zero, which means there are over 4 trillion possible IP addresses worldwide. Its representation typically consists of four decimal numbers separated by dots, with each decimal number ranging from 0 to 255.
However, as internet-connected devices continue to grow exponentially, there is a possibility of running out of IP addresses. To address this issue, ICANN created a new IP version known as IPv6. An IPv6 address is a 128-bit alphanumeric number, represented in hexadecimal notation and separated into eight groups of 16 bits by colons, resulting in a total of 128 bits. An IPv6 address appears like this: 2001:db8:1234::f350:2256:f3dd/64.
MAC Address
Another term you may have heard is MAC address, which stands for Media Access Control address. It is a 12-digit hexadecimal number assigned to the Network Interface Card (NIC) of every device that can connect to the internet. Like IP addresses define network addresses. MAC addresses define the address of a device such as your phone, laptop, or router.
Port Numbers
After learning about IP addresses, you may wonder, 'OK, my router can identify my device with an IP address, but what about the applications? For instance, if I am running 4-5 apps on my computer, how does my router identify which app to send data or from which app the request has been made? It does this with port numbers. Each application or service has its port number.
Port numbers are classified into three parts. The ports in the range from 0 to 1023 are well-known ports, meaning they are reserved ports for system purposes. The ports from 1024 to 49151 are registered ports, which are also assigned for specific services, so you cannot use them either. The ports from 49152 to 65535 are ephemeral ports. They are private ports that are not registered, meaning you can use them.
Firewall
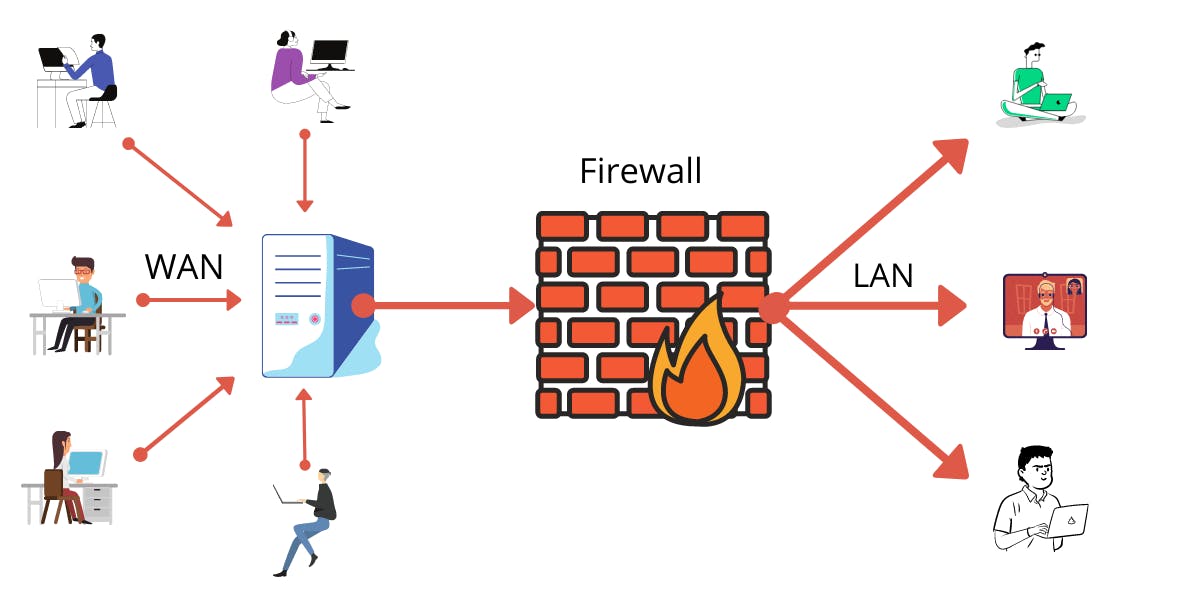
A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules. It acts as a barrier between internal private networks and external sources. Firewalls are primarily used to prevent malware and network-based attacks. These firewalls act as a gatekeeper. They monitor every attempt between our computer and another network. They do not allow data packets to be transferred through them unless the data is coming or going from a user-specified trusted source.
Firewalls are designed in such a way that they can react quickly to detect and counter-attacks throughout the network. They can work with rules configured to protect the network and perform quick assessments to find any suspicious activity. In short, we can point to the firewall as a traffic controller.
I hope you learned something from this blog. If you have, don't forget to drop a like, follow me on Hashnode, and subscribe to my Hashnode newsletter so that you don't miss any future posts. You can also reach out to me on Twitter or LinkedIn. If you have any questions or feedback, feel free to leave a comment below. Thanks for reading and have a great day!