Hey everyone, today we will explore OSI models - a fundamental concept in computer networking. In this blog, I aim to cover all aspects of OSI models that I have learned so far. I will explain the OSI model with the help of diagrams. I believe it's easier to understand with pictures and diagrams instead of long theories. As a computer science student, it is crucial to keep ourselves updated with the latest technologies. Hence, I recommend that you do your research after reading this blog to discover new and related concepts in computer networking.
Overview
The OSI(Open System Interconnection) model consists of seven layers. The OSI model was created to standardize and facilitate communication between different computer systems and networks. It was developed by the International Organization for Standardization (ISO) in the early 1980s. I will explain all seven layers of it, but before jumping straight into the OSI model, you need to know that the OSI model is not used in the real world. Yes, you read that correctly; the OSI model is not used in real life. Instead of that, we use another model called the TCP/IP model. It is similar to the OSI model, but it has four layers instead of seven layers. The diagram below will make things clear.

Application Layer 🚩
At the topmost layer of the OSI Model, we find the Application layer, which is where users interact with applications. The Application layer accesses network services via protocols such as SMTP (Simple Mail Transfer Protocol) to send emails, and POP3 or IMAP to receive emails.
Just remember that the Application layer interacts with the user and has access to network protocols. That's all you need to know for the Application layer. If you want to learn more, you can research how the protocols work and how the applications listen to them.
Presentation Layer 🚩
The second layer of the OSI model is the presentation layer. On this layer, data is received from the application layer. The presentation layer's role is to convert the data into a different format so that the receiver's machine can understand it. You might wonder why this conversion is necessary. It's because each machine can identify a different code. For example, the sender's machine may send ASCII (American Standard Code for Information Interchange) code, while the receiver's machine can understand EBCDIC (Extended Binary Coded Decimal Interchange Code) code. They are different formats, so it's necessary to convert the data formats.

This layer is responsible for data encryption and decryption. Encryption involves converting the plaintext data into ciphertext (unreadable format) before sending it to the receiver. The receiver then decrypts the data, making it readable again. This process ensures that our data remains safe and secure from hackers, as they are unable to read the encrypted data. Therefore, encrypting data is essential, and the presentation layer helps us accomplish this task.
Session Layer 🚩
The primary purpose of the session layer is to manage communication between two machines. It makes sure that sessions between these machines stay alive. A session represents the time that the two machines are connected. The session is terminated when this connection gets interrupted or broken. If, on the other hand, the intended operation is completed, the session is considered to be ended.

The Session layer handles the exchange of data between systems in full-duplex or half-duplex mode. It keeps a log of established connections for transmitting and receiving data, which is also known as dialogue management. The layer utilizes a token system, where the user sharing the data is assigned a token in case of half-duplex mode and, after the exchange, transfers it to another device. This token method ensures the efficiency of the connection.
Transport Layer 🚩
I believe I don't need to explain this in detail, as you likely already know the concept from its name. Nevertheless, there are several additional concepts I'd like to introduce. First, let's look at the role of the transport layer and its importance. The transport layer serves as an end-to-end mechanism for delivering messages to a host. It is called 'end-to-end' because it establishes a direct connection between the source host and the destination host, ensuring reliable service delivery, rather than relying on intermediate hops.
Note: In the Transport Layer, data is encapsulated in units known as segments.
Let's look at how the transport layer works on the client and server sides before dipping deeper into this layer.
Server Side working for Transport Layer:
We receive data from the application layer on the server side. The data is next segmented, which involves dividing it into segments, putting the source and destination port numbers into the segment's header, and ultimately transferring it to the Network layer.
Client Side working for Transport Layer:
We receive data from the Network layer on the client side. In this process, we rebuild the segmented data, read its header to identify the port number, and then send the data to the correct port in the Application layer.
The transport layer requires a Port number to correctly deliver the segments of data to the correct process amongst the multiple processes running on a particular host. A port number is a 16-bit address used to identify any client-server program uniquely. If you are unfamiliar with the port number or any other keyword I'm referring to, you can simply Google it, or you can check out my blog on the essential things to know before delving into the OSI model.
end-to-end connection:
The transport layer is responsible for establishing the end-to-end connection between hosts, primarily using TCP and UDP. TCP is a secure, connection-oriented protocol that employs a handshake procedure to establish a robust connection between two end hosts. It guarantees the reliable delivery of messages and finds applications in various scenarios. On the other hand, UDP is a stateless and unreliable protocol that provides best-effort delivery. It is suitable for applications with minimal concern for flow or error control and is commonly used when transmitting large amounts of data, such as in video conferencing or multicasting protocols.

Multiplexing and Demultiplexing:
Multiplexing (many to one) occurs when data from multiple processes from the sender are combined into one packet with headers and transmitted as a single packet. Multiplexing enables the usage of several processes running on a host over a network at the same time. The port numbers differentiate the processes. Similarly, when a message gets circulated among multiple processes, demultiplexing (one to many) is necessary on the receiver side. The transport layer accepts data segments from the network layer, distributes them, and delivers them to the relevant process operating on the receiver's system.

The above picture provides a full understanding of multiplexing and demultiplexing. Let's look into it. We have two applications, Hike and WhatsApp. For clarity, let's assume A is the sender, and B is the receiver, as mentioned in the diagram's source IP section. Both A and B have these applications installed on their smartphones.
Suppose A wants to send messages to B using both WhatsApp and Hike. To achieve this, A must specify B's IP address and the destination port number for WhatsApp while sending a message through the WhatsApp application. Similarly, for Hike, A must mention B's IP address and the destination port number specific to Hike while sending the message.
The messages from both applications will be combined with appropriate headers (such as source IP address, destination IP address, source port number, and destination port number) and transmitted as a single message to the receiver. This process is known as multiplexing.
Upon reaching the destination, the received message is unpacked, and constituent messages (i.e., messages from Hike and WhatsApp applications) are directed to the appropriate application based on the destination port number. This process is called demultiplexing. Similarly, B can also send messages back to A.
In summary, multiplexing is the process of combining multiple messages with headers into a single transmission, while demultiplexing involves extracting and directing individual messages to their respective applications based on their destination port numbers.
Congestion Control:
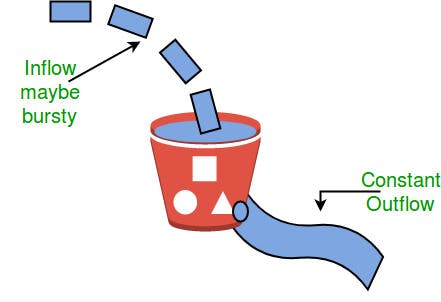
Congestion occurs when too many sources on the network try to transfer data, forcing the router buffers to overflow, leading to packet loss. As a result, resend of packets from the sources adds to the congestion. In this case, the Transport layer provides Congestion Control in a variety of methods. It uses open-loop congestion control to prevent congestion and closed-loop congestion control to reduce congestion once it has happened in a network. For congestion control, TCP offers AIMD - additive increases multiplicative decrease - and the leaky bucket technique.
I believe this blog post might become too lengthy. Therefore, I believe it's worthwhile to split it into two parts. Recently, I uploaded two long blogs, and it seems that some folks are feeling overwhelmed when they see the reading time. To address this, I am dividing it into two parts. The next part will be released soon and will be included in our computer networking series. If you enjoy the blog, please consider subscribing, liking, and sharing your thoughts about the blog and my writing. Additionally, if you are able, you can also sponsor me.